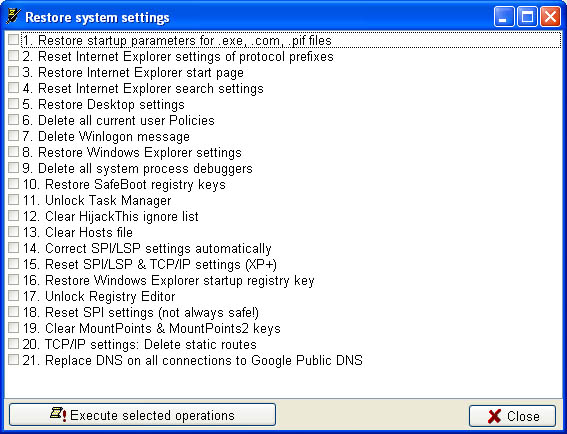
|
System Restore |
Home Previous Next |
System Restore is a special AVZ function that restores a number of system functions corrupted by malware.
System Restore microprograms are stored in the anti-virus database and updated as and when necessary.

The database currently contains the following microprograms:
1. Restore startup parameters for .exe, .com, .pif files
This microprogram restores system response to exe, com, pif, scr files.
When to be used: Programs have stopped starting since a virus was removed.
2. Reset Internet Explorer settings of protocol prefixes
This microprogram restores Internet Explorer settings of protocol prefixes.
When to be used: When you type in an address such as www.yandex.ru, it is substituted with an address of the following kind: www.seque.com/abcd.php?url=www.yandex.ru
3. Restore Internet Explorer start page
This microprogram restores the start page in Internet Explorer.
When to be used: The start page has been substituted.
4. Reset Internet Explorer search settings
This microprogram restores the search settings in Internet Explorer.
When to be used: When you click “Search” in Internet Explorer, the browser accesses some unwanted website.
6. Delete all current user Policies
Windows has a mechanism for limiting user actions, which is called Policies. This technology is exploited by many malicious programs, since settings are stored in the registry and are simple to create or modify.
When to be used: Windows Explorer functions or other system functions have been blocked.
7. Delete Winlogon message
Windows NT and later systems in the Windows NT line (2000, XP) let you specify the message to be displayed at startup. This is exploited by a number of malicious programs. Notably, removal of the malicious program does not remove this message.
When to be used: An unwanted message is displayed on system startup.
8. Restore Windows Explorer settings
This microprogram resets a number of Windows Explorer settings (settings modified by malware are reset first).
When to be used: Windows Explorer settings have been changed.
9. Delete all system process debuggers
Registering a system process debugger makes it possible to perform a hidden launch of an application. This is exploited by a number of malicious programs.
When to be used: AVZ has detected unrecognized system process debuggers. Problems arise when starting the system components, in particular, the desktop, disappears after reboot.
10. Restore SafeBoot registry keys
Some malicious programs, such as the Bagle worm, corrupt SafeBoot settings of the system. This microprogram restores the SafeBoot settings.
When to be used: The computer cannot be started in SafeBoot mode. Use this microprogram only when you are experiencing problems with system startup in SafeBoot mode.
11. Unlock Task Manager
Malicious programs lock the Task Manager to protect their processes from detection and removal. Using this microprogram removes the lock.
When to be used: The Task Manager has been locked. When you attempt to run the Task Manager, a message appears: “Task Manager Locked by Administrator”.
12. Clear HijacThis ignore list
The HijackThis utility stores a number of its settings in the registry, in particular the exclusions list. This is a malicious program need only register its executable files in the exclusions list in order to hide from HijackThis. A number of known malicious programs exploit this vulnerability at present. This AVZ microprogram clears the exclusions list of the HijackThis utility.
When to be used: Suspicions that the HijackThis utility does not display all system information.
13. Clear Hosts file
Clearing the Hosts file entails locating the Hosts file, removing all meaningful strings from it, and adding the standard string "127.0.0.1 localhost".
When to be used: Suspicions that the Hosts file has been modified by a malicious program. Typical symptoms: blocking of anti-virus application updates. You can control the contents of the Hosts file by using the Hosts File Manager built into AVZ.
14. Correct SPI/LSP settings automatically
This microprogram analyzes SPI settings and, upon detecting errors, corrects the errors automatically. This microprogram can be launched repeatedly an unlimited number of times. It is recommended to reboot the computer after running this microprogram. Please note: this microprogram must not be launched from the terminal session.
When to be used: Removal of a malicious program resulted in the loss of the Internet connection.
15. Reset SPI/LSP and TCP/IP settings (XP+)
This microprogram runs on Windows XP, Windows 2003 and Vista only. The principle of its operation involves resetting and recreating SPI/LSP and TCP/IP settings using the native Windows utility called “netsh”. For details on the resetting of settings see the Microsoft Knowledge Base: http://support.microsoft.com/kb/299357 Please note: Reset settings only if necessary, when removal of malware has resulted in problems with Internet access that cannot be resolved.
When to be used: Removal of a malicious application resulted in the loss of Internet access, and the microprogram “14. Correct SPI/LSP settings automatically” proved ineffective.
16. Restore Explorer startup registry key
This microprogram restores system keys of the registry responsible for Windows Explorer startup.
When to be used: Windows Explorer does not load on system startup, but explorer.exe can be launched manually.
17. Unlock Registry Editor
This microprogram unlocks the Registry Editor by removing the policy that prevents it from starting.
When to be used: You are unable to start the Registry Editor. Attempts to do so result in messages to the effect that the Registry Editor launch has been blocked by the administrator.
18. Reset SPI settings
This microprogram backs up SPI/LSP settings, deletes them and then recreates them using a template stored in the database.
When to be used: Severe corruption of SPI settings could not be fixed by scripts 14 and 15. Use only when necessary.
19. Clear MountPoints & MountPoints2 keys
This microprogram clears the MountPoints and MountPoints2 database in the registry. This operation can often help when disks do not open in Windows Explorer after infection with a Flash virus.
To perform restoration, check one or several items and click “Execute selected operations”. Clicking OK closes the dialog box.
Note: System Restore is useless when the system is infected with a trojan that is corrupting settings. Remove the malicious program before restoring system settings.
Note: Removing traces of most hijackers requires running three microprograms: “Reset Internet Explorer search settings”, “Restore Internet Explorer start page”, and “Reset Internet Explorer settings of protocol prefixes”.
Note: You can run any microprogram multiple times in a sequence without damage to the system. Exceptions: ”5. Restore desktop settings” (this microprogram resets all desktop settings, so you will have to choose the desktop background color and wallpaper again) and “10. Restore SafeBoot registry keys” (this microprogram recreates registry keys responsible for system startup in SafeMode).